
Comparing Base64, Morse Code, and ROT13: A Beginner’s Guide to Cipher Tools
January 11, 2025You may soon find yourself in need of an anti-virus software solution. Here, we will discuss a few options available. What Are Your Anti-Virus Options & Threat Maps?
Comparing Anti-Virus Software
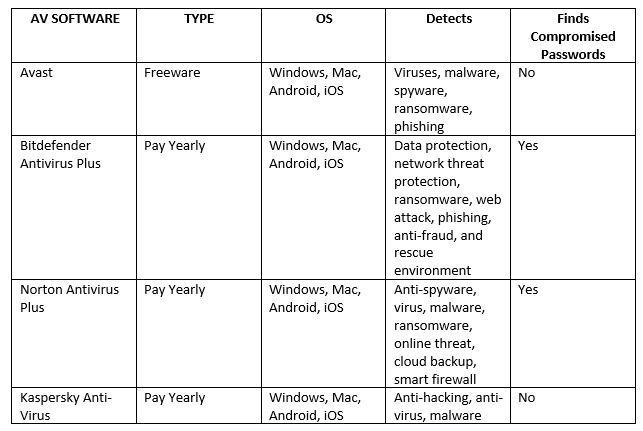
For the last 5 or so years, Anti-virus software has not been a concern of mine. With the upgrades of Microsoft’s Windows Security, I have entrusted my computers security to be protected. Window’s Security Defender stacks up and excels to competitors that require a yearly subscription. The major aspects that stands out in comparison to the AV products above, is that Windows Security is only compatible with Windows 10.
Microsoft Windows Security boasts Next-gen antivirus and malware defense. Tracking prevention, Biometric login, and all built in, always updated, and at no extra cost to the customer. Windows Security offers secure sign-in with face scan, online privacy with their web browser Microsoft Edge, and automatically backs up on the cloud in OneDrive. After a bit of research, however, I see I may be lacking some potential protection that might not be offered with Microsoft Windows Security. Seeing the above features I would recommend using Microsoft Windows Security that is compatible with a 3rd party AV product such as an Endpoint detection and response in block mode, which will provide added protection from malicious artifacts.
Threat Maps
The four online cybersecurity threat maps that we are comparing are Netscout, Check Point, Kaspersky, and FireEye Cyber Threat Maps. Cybersecurity threat maps are visually appealing. They each provide a map that shows real time attacks that are currently taking place, with nice looking colors. Kaspersky is different from the other three in that the map is 3D while the others are 2D.
Each map provides information such as attack type, attack starting location and end point, number of daily attacks, top targeted countries, top targeted industries, and top malware types. However, Netscout offer the user a breakdown of event type sych as UDP, TCP SYN, IP fragmentation, DNS, IPv4. Kaspersky’s map provides information such as OAS, ODS, MAV, WAV, IDS, VUL, KAS, BAD, and RMW.
The most difficult map to use would be the Kaspersky map. This is due in part to its features and depth of the map. The Kaspersky map is by far and large the better map for multiple reasons listed above. However, with Kaspersky providing a superior product, I would not solely suggest using this map alone. Using all 4 maps will provide a higher probability for accuracy and all 4 are inconsistent in the data provided for top countries attacked and top reported attacked industries. While using these strengths together, one may deduce which type of attacks they should prioritize while setting up their home or work system or network.
As visually appealing as the threat maps may be, they do not serve much real time use for location. There is also speculation that many maps claim to show real time data, but in reality, most are simply a playback of previous attacks. Also, a major weakness with the above threat maps is the fact that most threats and attacks are anonymized by masking their real locations. Therefor, what is displayed on the map would be incorrect.
For more information just like this, find more of my work at https://TrustITSec.com
LINKS




